For tech enthusiasts, diving deep into the workings of our favorite apps and programs is thrilling. Yet, with this curiosity often comes a pressing concern: how do these applications stay secure against evolving cyber threats?
The answer lies in a crucial concept known as Code Integrity. In this guide, we’ll take you through the essentials of both code integrity and software integrity, exploring their importance, mechanisms, and role in building secure, quality software. Plus, we’ll discuss how using tools like Cron Jobs can streamline processes in the lifecycle of software integrity.
Understanding the Basics
Let’s start with the basics. Code integrity is like the bouncer at the entrance of a high-security club for software.
Just as the bouncer allows only authorized individuals to enter the club, code integrity also ensures that only trusted and unaltered code gets executed on your devices, It acts as a defence mechanism against malicious actors who try to tamper with software to inject their malicious code.
Why Does It Matter?
Picture this: You’re downloading a new app that promises to revolutionize your productivity. You install it, but behind the scenes, the app’s code has been tampered with, compromising your data and privacy.
Scary, right? That’s where code integrity swoops in as the hero. By guaranteeing that the code running on your device is the same code the developers intended, it creates a secure environment for your digital activities. Hence, It should be a fundamental part of any software development team’s workflow.
The Role of Cron Jobs in Code Integrity Checks
A powerful tool in the software world, Cron Jobs allow developers to schedule automated tasks, making them invaluable for regular code integrity checks. Here’s how cron jobs fit into the code integrity workflow:
-
Regular Integrity Scans: Schedule regular integrity checks, verifying checksums and digital signatures to detect any unauthorized changes in the code.
-
Automated Code Updates: Cron jobs can automate the process of updating code with verified, digitally signed patches, ensuring ongoing code and software integrity without manual intervention.
-
Security Alerts: Automate alerts to notify developers of potential security breaches or code changes detected during integrity checks.
The Key Mechanics of Code Integrity
Now that we grasp the importance of code integrity and code quality, let’s delve into their inner workings.
-
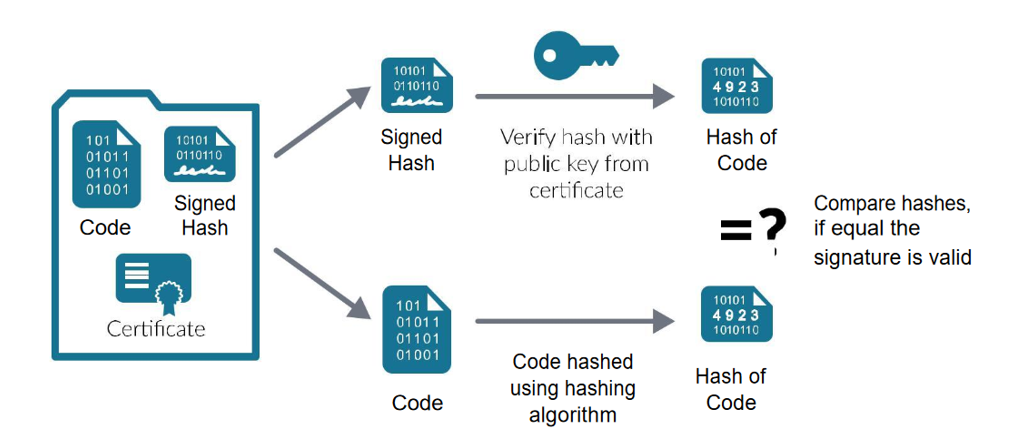
Digital Signatures: When developers create software, they generate a unique digital signature for it. This signature acts as a virtual seal of approval, confirming that the code is legitimate and hasn’t been tampered with. Digital signatures play a crucial role in verifying the authenticity and integrity of software components.
-
Checksums: Checksums serve as digital fingerprints of the code, helping verify its authenticity. A checksum is calculated based on the contents of the code, and even a minor alteration results in a significant change in the checksum. By comparing checksums, developers can detect unauthorized modifications to the code.
-
Code Signing: This process involves developers signing code with a private key. Your device can verify this with a public key, ensuring only authorized code runs on it. It’s a vital layer of defense against unauthorized modifications.
Layers of Protection
Code integrity isn’t a one-size-fits-all solution. It comes in different flavours, each offering varying levels of protection. One popular method is "code signing," where developers sign their code with a private key, and your device verifies it using a corresponding public key. This process ensures that only authorized code can run, thus safeguarding against unauthorized modifications.
A few more important steps can be taken: –
- "Source code protection" refers to the actions undertaken to safeguard a computer program’s source code against unauthorized tampering or theft. These protective measures encompass a blend of digital and physical security tactics, ranging from encryption and authentication protocols to controlling access to the source code.
- "Code coverage" is a measure that quantifies the proportion of code lines tested by automated tests relative to the total number of lines in the project.
- The Software Development Life Cycle (SDLC) comprises phases like creation, testing, and release. It involves requirements gathering, design, development, testing, deployment, and maintenance. SDLC is a framework that manages software development for timely, budget-friendly, and quality outcomes.
- The documentation process comprises writing detailed and understandable descriptions of the code’s goals, features, and implementation. Design papers, user guides, API documentation, and any other documentation that aids developers in understanding and modifying the code are considered documentation.
- Static code analyzers are only one kind of code quality tool that may be used to check for things like coding mistakes, security flaws, and performance bottlenecks. These technologies may be included in the software development lifecycle to streamline the process of finding and fixing bugs in the code.
- Establishing coding standards can greatly ensure code quality. These standards cover naming conventions, formatting, error handling, and more, all contributing to consistent and maintainable code.

Building Trust in Software
The world of software is built on trust. We trust that our applications will perform as expected and that our data won’t be compromised. Code integrity contributes significantly to this trust by minimizing the risks associated with malicious software modifications.
- User Confidence: When you know that the software you’re using has undergone rigorous integrity checks, you can use it with confidence. It’s like knowing your favourite restaurant meets health and safety standards – you can enjoy your meal without worry!
- Preventing Unauthorized Access: Imagine a world where malware couldn’t infiltrate your system due to robust measures. We’re not quite there yet, but such measures drastically reduce the attack surface for hackers, making their job much harder.
- Secure Software Supply Chain: Developers often rely on third-party libraries and components to build software. With code integrity, these components are verified, ensuring they don’t carry hidden vulnerabilities or malicious code.
Challenges and Future Directionsin Code and Software Integrity
Of course, no superhero is without their challenges. Despite their importance, code integrity and code quality face several challenges in the ever-evolving landscape of software development and cybersecurity. As technology advances, so do the tactics of malicious actors. Let’s examine some of these challenges and potential future directions for addressing them: –
-
Balancing Security with User Experience: One of the primary challenges is striking the right balance between security and user experience. Stringent security measures, while essential for protecting against cyber threats, can sometimes impede usability and convenience. Finding the optimal balance between security and user experience remains a constant challenge.
-
Evolving Attack Techniques: As technology advances, so do the tactics employed by malicious actors. Cyber threats continue to evolve, posing new challenges to code integrity and security measures. Attackers may employ sophisticated techniques such as zero-day exploits, social engineering, and supply chain attacks to circumvent existing defenses.
-
Complexity of Software Ecosystems: Modern software ecosystems are increasingly complex, with numerous dependencies, integrations, and interconnections. Managing the security and integrity of such ecosystems poses significant challenges, as vulnerabilities in one component can potentially cascade throughout the entire system.
But don’t worry, cybersecurity experts are always on the lookout for innovative ways to stay one step ahead. In the future, we might witness advancements in AI-driven code analysis and even more sophisticated ways to validate software integrity.
Additionally, increased collaboration between developers, security professionals, and end-users will further strengthen code integrity practices.
Conclusion
In conclusion, code integrity and code quality are foundational pillars of software development, essential for building trust, ensuring security, and delivering reliable, maintainable software. From the mechanisms of digital signatures and checksums to the layers of protection provided by code signing and source code protection, these concepts form the backbone of secure software ecosystems.
As we navigate the complex landscape of cybersecurity threats and technological advancements, it’s imperative to remain vigilant and proactive in safeguarding software integrity. By embracing best practices, adopting robust security measures, and fostering collaboration across the industry, we can mitigate risks, enhance trust, and uphold the integrity of our digital experiences.
In the dynamic realm of software development, Code Integrity and Software Integrity are crucial for building secure, reliable applications. From mechanisms like digital signatures and checksums to using tools like cron jobs for regular integrity checks, these practices lay the foundation for a safer digital experience.
As we continue to face new cybersecurity challenges, it’s essential to uphold these principles, fostering an environment where technology empowers rather than endangers our digital lives. Prioritizing security, quality, and innovation will guide us toward a future of trusted, integrity-first software.
FAQ
What is the difference between code integrity and code quality?
Code integrity focuses on ensuring the security and trustworthiness of software by verifying the authenticity and integrity of the code. On the other hand, code quality pertains to the reliability, maintainability, and efficiency of the code, ensuring that it is free from bugs, vulnerabilities, and unintended behaviors.
What are some challenges faced by code integrity and code quality?
Challenges include balancing security with user experience, evolving attack techniques employed by malicious actors, and managing the complexity of modern software ecosystems with numerous dependencies and integrations.
How does code integrity contribute to building trust in software?
Code integrity minimizes the risks associated with malicious software modifications, thereby fostering trust among users. When users know that the software they’re using has undergone rigorous integrity checks, they can use it with confidence, leading to a positive user experience and enhanced trust in the software.


Leave a Reply